Deploying and using Azure Bastion to secure access to Azure VMs
Azure Bastion is great.
If you've not heard of it, you're in for a treat. Azure Bastion is a PaaS (Platform as a Service) offerring which provides secure access to your VMs, using either RDP or SSH directly from within the Azure portal.
Bastion is provisioned directly within your virtual network (VNet) and provides you access via SSL and without exposing your VMs to the internet with a public IP. Bastion supports RDP and SSH - including SSH key authentication.
How much does it cost though?
You'll be surprised - and not in a bad way!
Reviewing the pricing for Azure Bastion for the UK South region in GBP shows that the bastion host itself costs £0.142 per hour and the first 5GB per month of data transfer costs nothing. Further pricing can be found on the linked page.
Setting it up
As Azure Bastion integrates within your VNet, you need to ensure it has enough address space within your VNet. In my demo subscription I have the following:
VNet with a 10.0.0.0/16 address space with the following subnets:
ActiveDirectory - 10.0.10.0/28
CoreServers - 10.0.11.0/24
Clients - 10.0.20.0/24
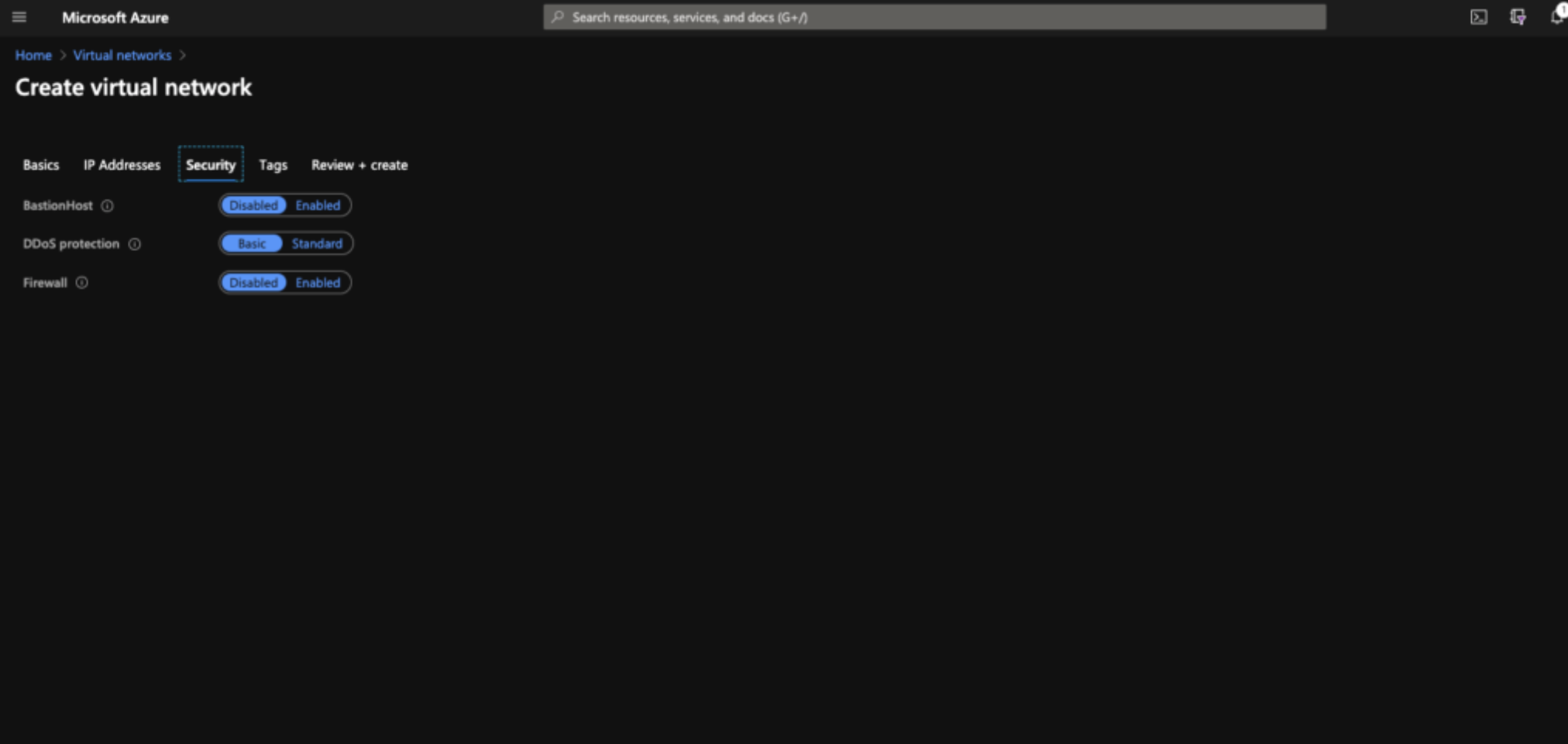
AzureBastionSubnet - 10.0.10.192/26
Azure Bastion requires a subnet of at least /26 to provide enough IPs for facilitating multiple connections. Bastion also requires a public IP address - this is for you to use to access it!
There are a couple of different methods to create a Bastion Host. You can do so during the creation of a VNet, or by creating a Bastion manually and associating it to a subnet.
How to use it
Once you've got your Bastion Host created and associated to a VNet, simply go to a VM within that VNet and hit "Connect". You'll see the below:
When you press "Bastion" you'll be presented with a username and password form to complete. As this VM is Windows, that's what shows up however if it were Linux it would show an option to use SSH Username/Password or SSH Public Key.
Once you enter credentials, you'll be logged in.
Thats it! As the Bastion connection is HTML5, it will also scale to whatever device you're logged in from.
Overall I think Bastion is a great solution to allowing access to VMs for external organisations, such as an external IT support company without requiring VPN setup and troubleshooting any potential issues with connecting to the VPN.
For more info, I'd suggest reviewing the Azure Bastion page here.