Managing non-Azure virtual machines using Azure Arc and Windows Admin Centre
Recently, I’ve been spending a good amount of time managing non-Azure virtual machines via Azure Arc and stumbled across something which I think is a really nifty feature. I thought I’d share for those who may not have known about this feature.
I also thought I’d make a series about using deploying the various features within Azure Arc, so consider this the first episode in the series!
Azure Arc?
For those that don’t know, Azure Arc is a free service that you can use to easily onboard your non-Azure machines to various Azure services such as Azure Monitor, Defender for Endpoint (Servers) and others. Arc works by installing the Azure Connected Machine agent on your non-Azure machines. You can onboard any non-Azure machine, such as a physical server, virtual server, VM in another cloud such as AWS/GCP, or VM in a private cloud.
Windows Admin Centre
Or “Center” for my American friends.
Windows Admin Centre (WAC) is a web-based management platform for Windows Server. You can perform most server management tasks using WAC, such as installing roles/features, restarting services, creating/deleting files. WAC also includes numerous extensions, such as OEM-provided extensions for physical servers that allow you to monitor things like disk health. I personally think WAC is a great way to reduce the burden when more than a handful of VMs, because as an admin, you don’t have to RDP in to each server to get the task done. It also works quite well for delegating access to other teams, such as a 1st/2nd line support team.
Combining the two to achieve VPN-less, secure server management
When the above two features are combined, however, it provides a great method to manage your server estate remotely, without the need for a VPN, but while remaining secure. How? Well, I’ll go into the details below and we’ll walk through getting it set up, but for the impatient among you, Azure Arc and WAC combined allow you to access your server over the internet using WAC, enabled by Arc. You can login to the Azure portal from anywhere in the world (adhering to any conditional access policies!), manage your server, and if needed, RDP into the server.
Sounds great - how do I get it set up?
I’m glad you asked!
First step is, of course, to have a non-Azure machine. As mentioned previously, this can be a physical server, a virtual server, but it can’t be running in Azure. For my example, I’m just going to create a small Windows Server 2019 VM on my physical host, but in your scenario it might be a server rack, a colocation facility, or something else.
I’m going to assume that you know how to set up a Windows Server machine, and therefore I won’t be going through this, but for the purposes of this demonstration I’m going to use three Windows Server virtual machines. One will be running the desktop experience as a domain controller, one will be running the desktop experience as a file server, and the other will run server core. Both Arc and WAC support server core installations. Both file servers will be joined to the domain.
Onboarding the machines to Arc
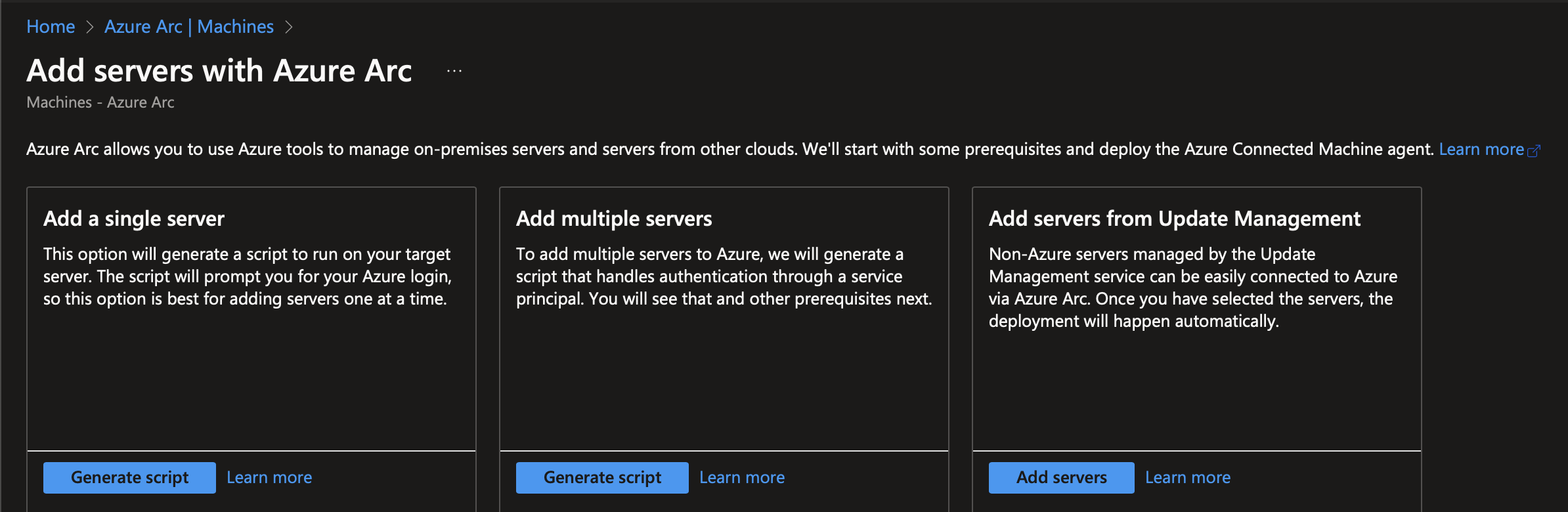
The first step is to get your machines onboarded to Azure Arc. You use a script for single server or multiple servers. As this is a small environment, I’m just going to use the single server script but if you were to do this at scale, I’d recommend the multiple server script. The key difference is that the single user script prompts for authentication each time, whereas the multiple server script creates a service principal and uses that to authenticate and onboard.
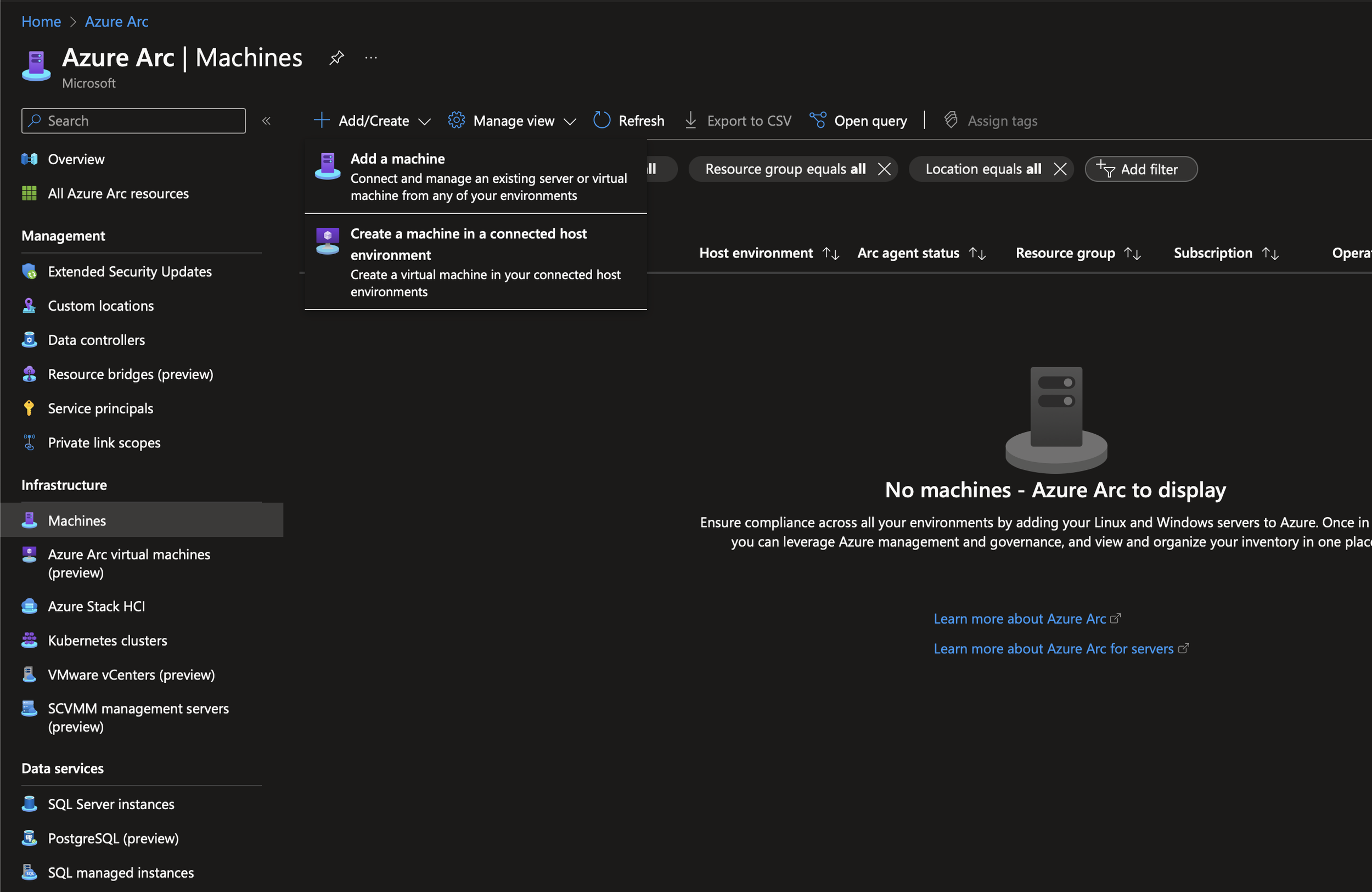
Create your resource group to store your Arc machines in. Mine is called Arc-RG. Once done, navigate to Azure Arc > Machines > Add > Add a machine
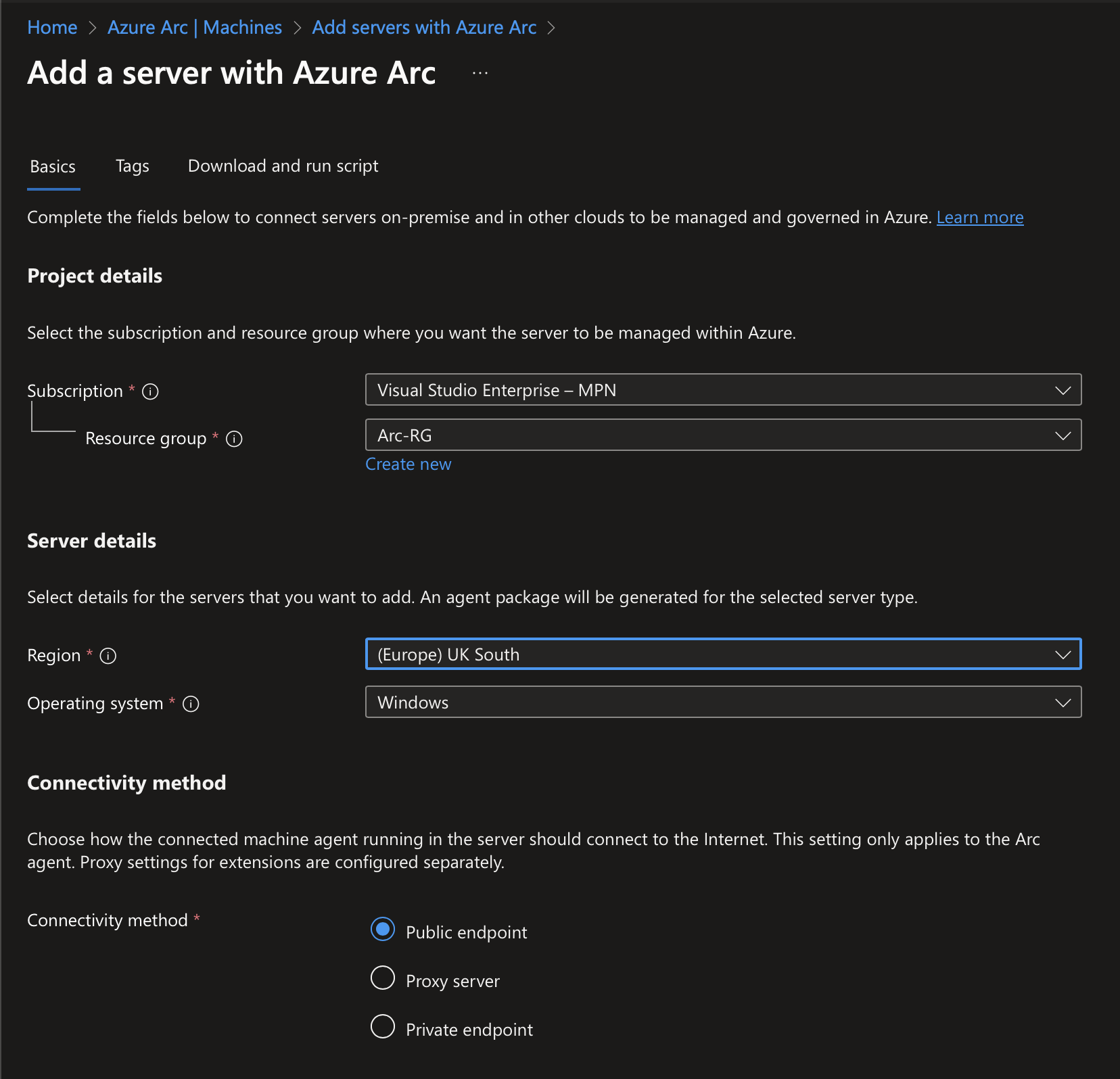
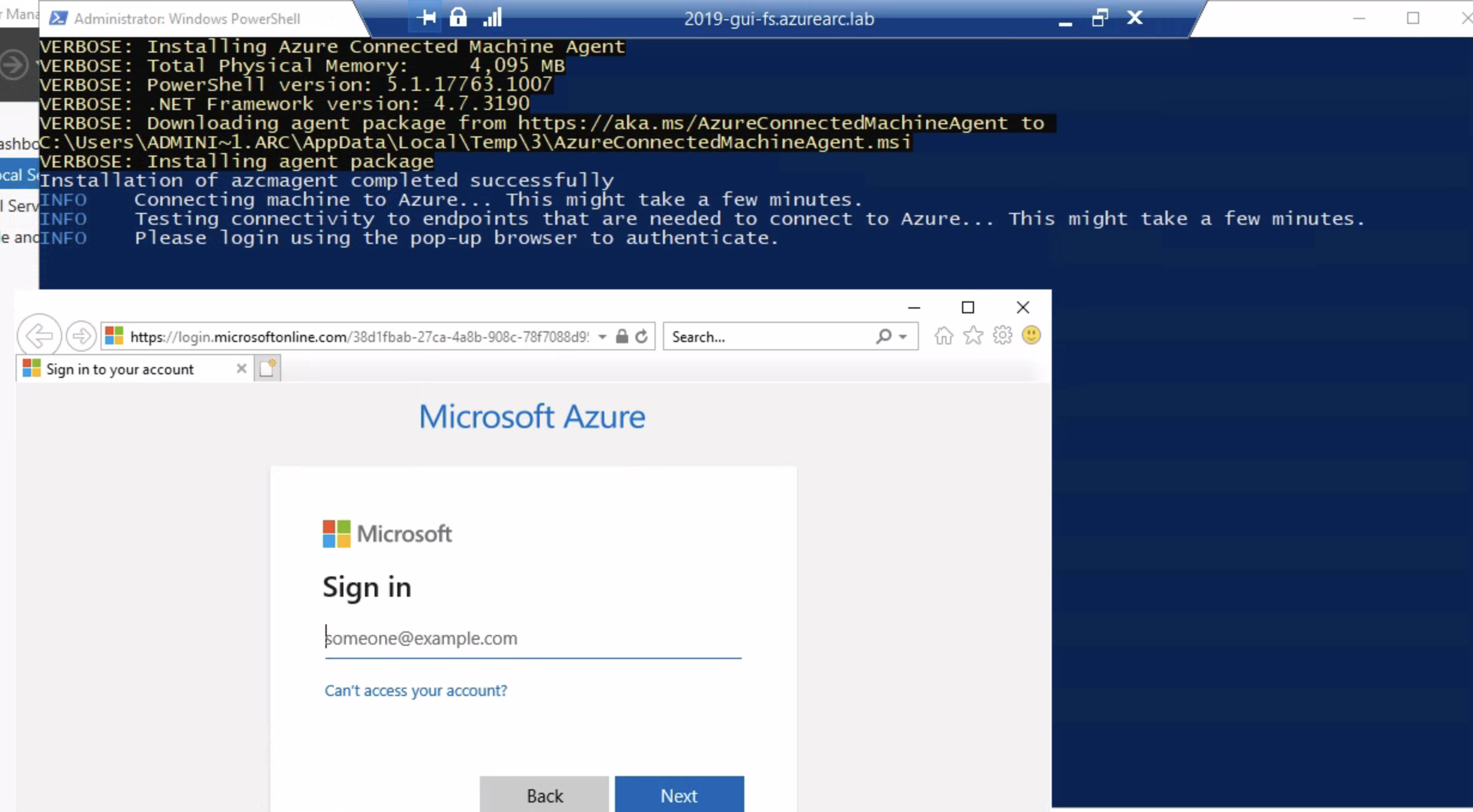
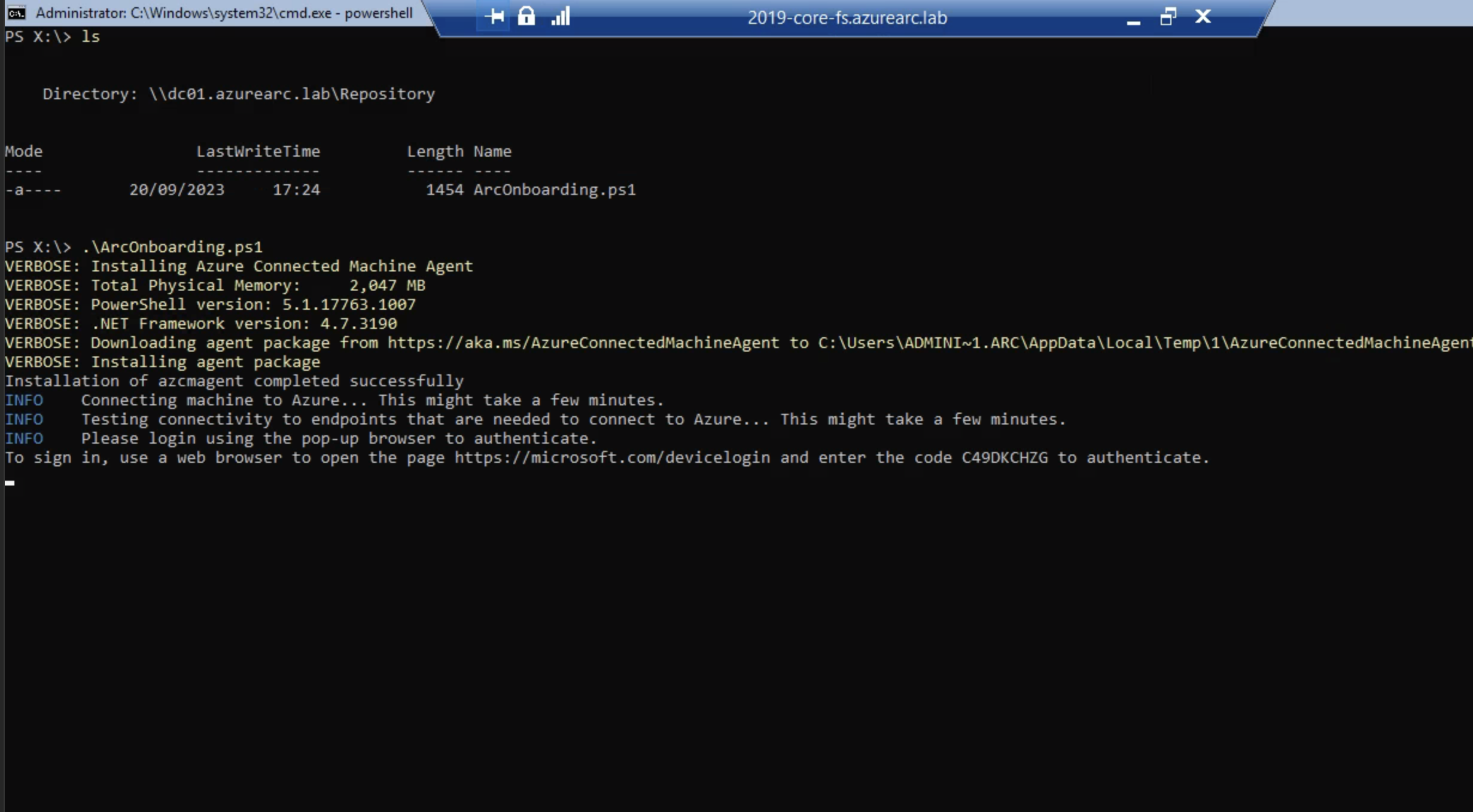
Once you select the single server script, you’ll need to enter in information such as your subscription, resource group, region, access method (public/private/proxy). This sets the variables within the script. Once you’ve got the script, download it to your machines and run it. You’ll notice a slightly different experience for server core versus desktop experience. As server core does not have a web browser, it prompts for device code authentication, whereas desktop experience does have a web server and so it prompts using Edge.
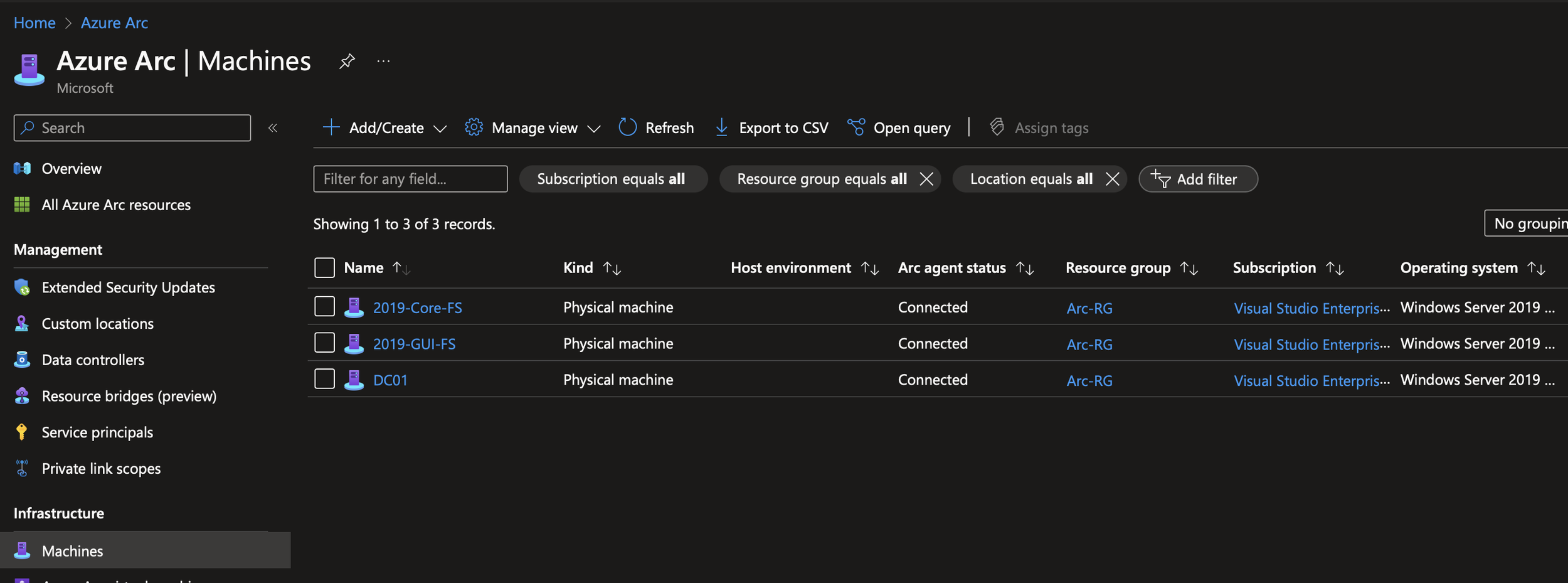
Sign in and the machine will start to onboard. Once onboarding is complete, the machine will light up in the Arc portal within a few minutes.
Success! You’ve onboarded your machines to Arc.
Installing the WAC Extension
The next step is a nice and simple one, installing the Windows Admin Centre extension.
Simply select your Arc machine, and select the Windows Admin Centre blade, then press the “Set up” button. You’ll be prompted to choose a listening port for WAC to listen on, and then the extension will install. In my experience, it takes around 10 minutes to install.
While it’s installing, you’ll also need to grant yourself the “Windows Admin Center Administrator Login” RBAC role, so feel free to do that while you wait.
Managing the server using WAC
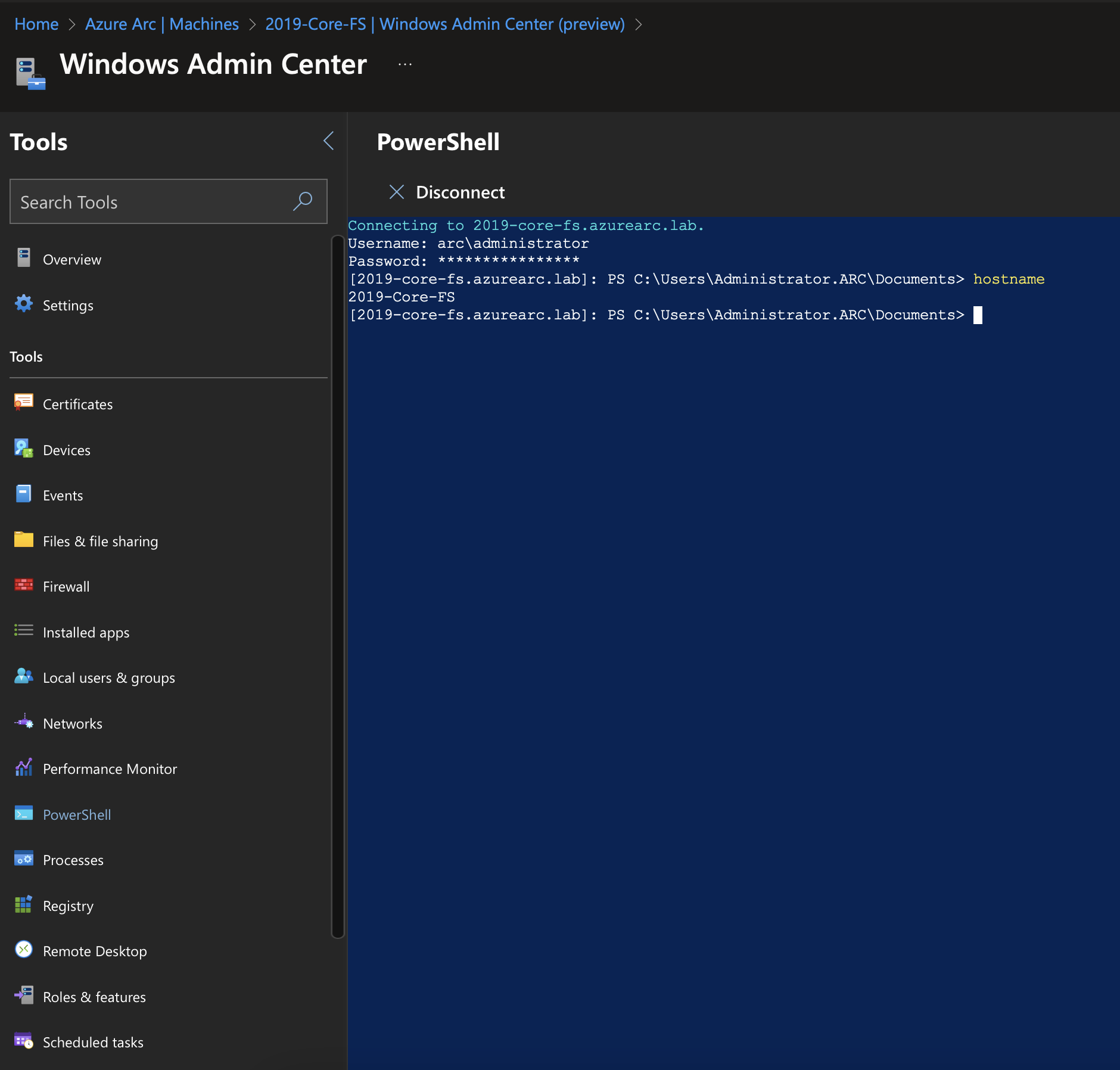
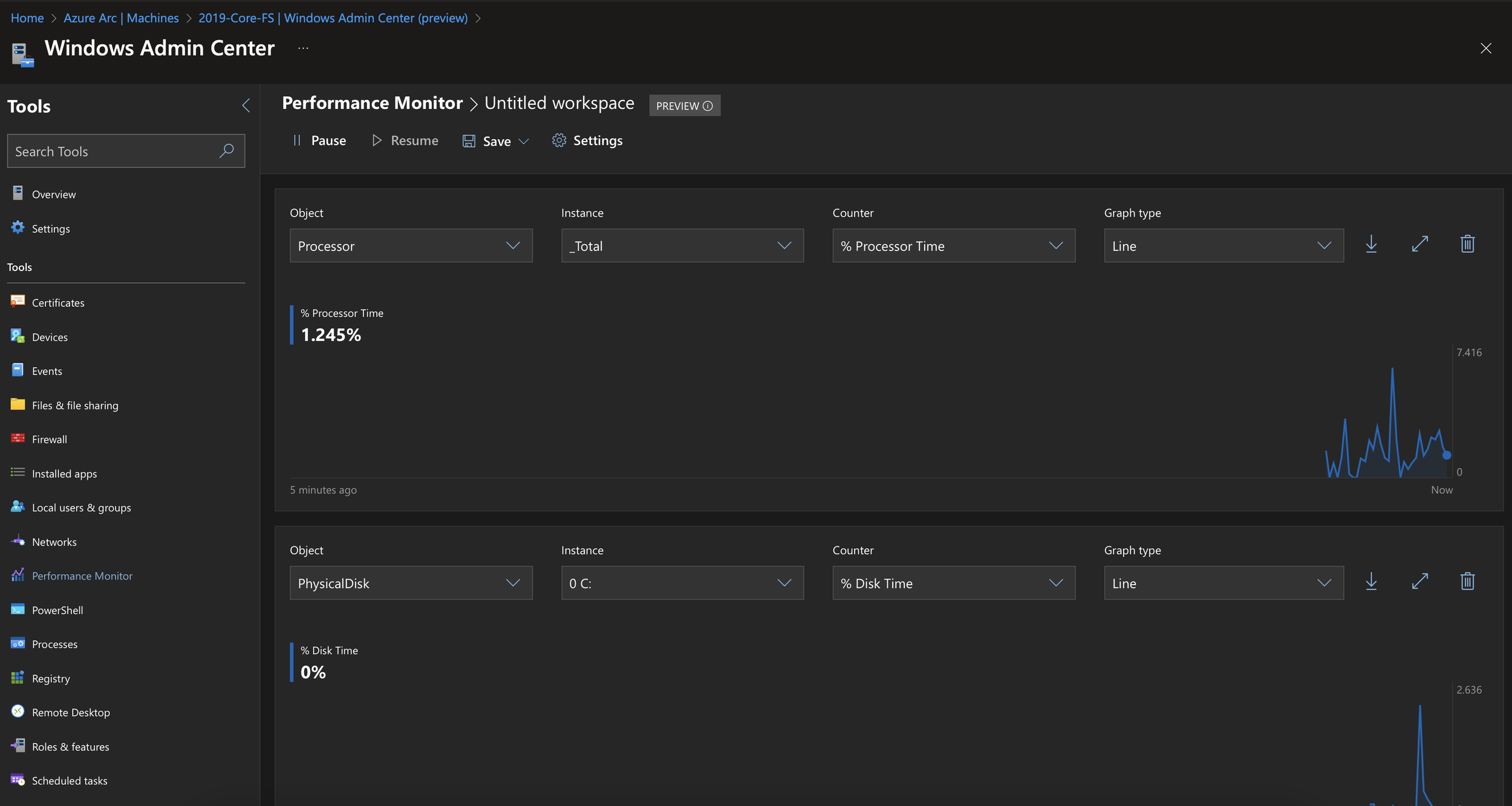
Once the WAC extension is installed, you’ll see a “Connect” button. Simply connect and you’ll be connected to WAC. From here, you can perform a number of administrative tasks, such as viewing/creating files, create/view/delete firewall rules, manage storage, install updates, and you can also use the WAC connection via Arc to RDP and perform remote PowerShell.
All of this is possible without the need for a VPN.
Wrapping up
As you can see, being able to leverage Azure Arc and WAC together allow you to manage your server without requiring VPN or local network access, all while network communication is secured using the Azure Arc (Connected Machine) agent.
I hope you’ve enjoyed this article. As mentioned, it’s the first in a series I’ll be doing. The series will be tagged with the category of “Azure Arc Series”, so if you’d like to view all posts in the series, simply click the category name at the top of the page.
Comments and feedback are welcome, as always.
Until next time.